Digital identities for IoT products
Use EJBCA PKI instead of OpenSSL and self-signed certificates while developing your IoT solution to ensure long-term scalability and security.
Challenge
Establish mutual trust between connected devices
To ensure cybersecurity in IoT solutions, edge devices, gateways, and servers must be capable of establishing mutual trust as well as trust in the firmware and software they execute.
This can only be achieved by equipping each system with at least a unique and secure digital identity. It must be small enough to be hosted inside a limited memory, strong enough to comply with the latest cybersecurity standards, and easy to check so that even small devices can verify who they are talking to and whether their firmware is genuine.
It must also be capable of supporting the derivation of robust session keys without exposing any secrets over any channel, and flexible enough so that every company can draw their own private circle of trust and decide who can enter or intersect with it. The technology does exist: it is called “private-public key infrastructure” and the digital identities are “digital certificates” following the X.509 standard.
As a developer of connected devices and machines or a cybersecurity expert supervising their deployment and operational security, implementing such technology is essential to safeguard against potential cyber threats. Modern industry standards and recommendations call for PKI and X.509 certificates to secure and authenticate communication, software, and supply chains for IoT. Examples of such standards and recommendations are:
- IEEE802.1AR - definition of IdevID and LDevIDs, respectively initial device certificate issued/injected by the OEM PKI and operational certificates issued and renewed by the operator PKI.
- Matter - usage of two chains of certificates, DAC and NOC respectively device attestation certificate issued/injected by the OEM PKI and node operational certificates issued and renewed by the network commissioner PKI.
- HTTPS, MQTTS - securing HTTP and MQTT with the mutual (D)TLS protocol using X.509 certificates provisioned on both sides by their respective PKI.
- IEEE1609.2, C-ITS, ITS - standardization of digital security for vehicle-to-anything (V2X) communications making extensive usage of PKI and certificates.
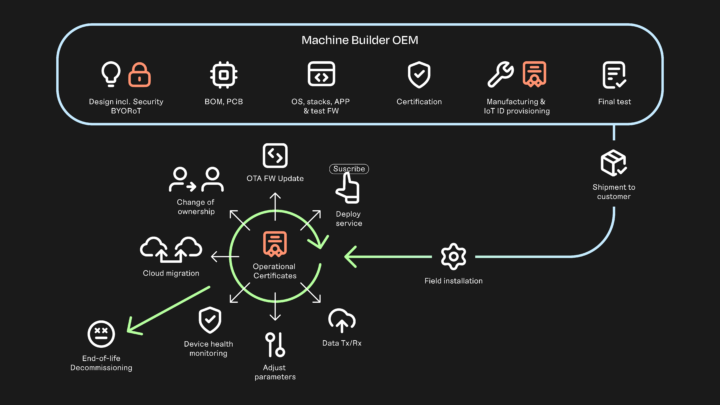
Solution
Issue and manage certificates for your IoT devices in production and operations
While free certificate issuance tools and self-signed certificates may be convenient for software development test purposes, they are not recommended for deployment. Unlike a PKI, self-signed certificates cannot draw the private circles of trust expected by all the standards. EJBCA is scalable, enterprise-grade, and easy to deploy, also for testing and prototyping as well as production purposes.
Using our best practices how-to and videos, you can set up a PKI to issue certificates for your industrial infrastructure and IoT devices. Once you're up, you can start tailoring your PKI and you'll have a fully functional PKI, including Certificate Authorities, roles, certificate profiles, a configured use case/issuing protocol, revocation support, and system documentation.
Get started with video tutorials and how-tos:
- Get started with birth identities based on IEEE 802.1AR (soon available)
- Get started with Matter IoT
- Certificates for TLS and mTLS, manually or via REST
Tutorials
Get inspired
Stay up to date with the latest news and blog articles, and find out about upcoming events related to EJBCA.

Tech Update: IEEE 802.1 AR, streamlining device identity management with EJBCA and certificate issuance

Hey Engineers and Developers – We have a new Helm chart for EJBCA deployment

Unveiling the Latest Tech Tweaks in Bouncy Castle Cryptographic APIs
Related open-source projects

Open-source signing software
Try SignServer for digital signing for code, documents, timestamps, and more. SignServer is a digital signing engine, making it easy for teams to automate signing workflows and support all of their signing formats and use cases.
Open-source cryptographic APIs
Bouncy Castle is one of the most widely used FIPS-certified open-source cryptographic APIs for Java and C#, allowing developers to integrate PKI security into their applications easily.